In today's digital and interconnected era, the healthcare sector operates in a landscape of security risks. In 2023 alone, the number of vulnerabilities uncovered in medical devices jumped by 59% to 993 issues. Consequently, the U.S. Food and Drug Administration (FDA), the European Commission, and other governmental agencies have issued cybersecurity guidelines for medical devices. Many of these guidelines advocate for fuzz testing as a means of vulnerability detection.

Cybersecurity Risks Inherent to Medical Devices
Malfunctioning medical software can pose significant risks to patient well-being. Numerous healthcare applications continue to operate on outdated operating systems, intensifying cybersecurity concerns.
From ransomware attacks to data breaches, these threats not only compromise patient data, but also pose significant risks to patient safety and the integrity of healthcare systems. According to the report “2023 State of Cybersecurity for Medical Devices and Healthcare Systems,” in 2023 there were 993 vulnerabilities within 966 medical products and devices, which is a 59% increase from 2022. 64% of these vulnerabilities were found in software.
 993 vulnerabilities were found in 2023 spanning 966 healthcare products; these vulnerabilities can potentially be exploited by attackers to target healthcare organizations. Source
993 vulnerabilities were found in 2023 spanning 966 healthcare products; these vulnerabilities can potentially be exploited by attackers to target healthcare organizations. Source
Another research that analyzed the National Vulnerability Database predicts an increase in the number of new critical vulnerabilities in medical devices and software in 2024 and 2025.
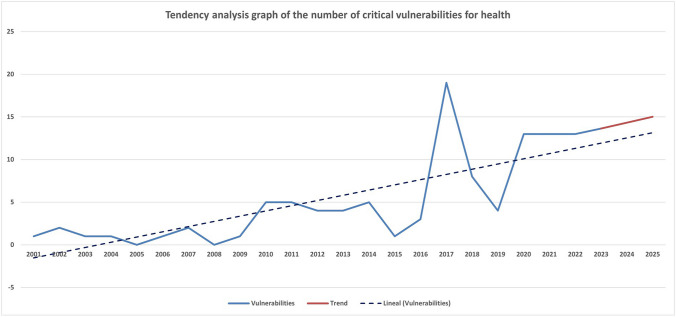 Security vulnerabilities in healthcare: an analysis of medical devices and software, 2023. Source
Security vulnerabilities in healthcare: an analysis of medical devices and software, 2023. Source
Reasons enough for the U.S. Food and Drug Administration (FDA) and the European Commission to create guidance documents to take proactive steps to enhance the cybersecurity of medical devices.
FDA guidance on cybersecurity in medical devices
The FDA's guidance document, titled "Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions," underscores the importance of integrating cybersecurity measures into the design and development of medical devices throughout their lifecycle. At the heart of the FDA's recommendations lies the adoption of a Secure Product Development Framework (SPDF), which aims to reduce vulnerabilities (by testing) and mitigate emerging cybersecurity risks.
Key to the SPDF is the implementation of robust security testing methodologies.“Security testing documentation and any associated reports or assessments should be submitted in the premarket submission.” FDA recommends the following types of testing be considered for inclusion in the submission:
- Security requirements;
- Threat mitigation;
- Vulnerability Testing (such as section 9.4 of ANSI/ISA 62443-4-1); and
- Manufacturers should provide details and evidence of the following testing and analyses:
- Abuse or misuse cases, malformed and unexpected inputs;
- Robustness
- Fuzz testing - Attack surface analysis;
- Vulnerability chaining;
- Closed box testing of known vulnerability scanning;
- Software composition analysis of binary executable files; and
- Static and dynamic code analysis, including testing for credentials that are “hardcoded,” default, easily guessed, and easily compromised.
- Abuse or misuse cases, malformed and unexpected inputs;
- Penetration testing
- Manufacturers should provide details and evidence of the following testing and analyses:
To this effect, the FDA proposes to consider fuzz testing as a vulnerability testing method to test and analyze cases of misuse or abuse and malformed and unexpected inputs.
- Key US cybersecurity standards for medical devices
- When manufacturers need to comply with the FDA's cybersecurity requirements
- Fuzzing's role in the FDA's guidance and AAMI TIR 57:2016
- 4 reasons why fuzzing is highly recommended for medical devices.
What is fuzz testing?
Fuzz testing, also known as fuzzing, is a dynamic software testing methodology used to uncover vulnerabilities and defects in software applications, this also includes Class I, II, and III medical devices. Fuzzing involves providing random, unexpected, or malformed inputs to a software application to observe how it behaves under such conditions.
Similar to unit testing, the software is tested under various scenarios. The key difference is that unit testing is deterministic, meaning that the expected outcome is known in advance, while fuzz testing is non-deterministic or exploratory, meaning that the expected outcome is not necessarily known ahead of time. This makes fuzz testing useful for uncovering bugs and security vulnerabilities that may not have been identified through other testing methods. Watch this video to learn how to mock embedded systems like medical devices with fuzz data.
By subjecting medical device software to fuzz testing, developers can identify potential vulnerabilities, security flaws, and unexpected behavior that could be exploited by attackers or cause malfunctions in medical devices.
Why fuzzing is recommended for testing medical devices
Fuzzing is especially efficient in testing embedded systems, including medical equipment and devices. Why so:
- Fuzz testing increases and calculates code coverage
By leveraging feedback about the software under test, modern fuzzers can actively craft test inputs that reach up to 100% code coverage. Apart from reaching critical parts of the tested code more reliably, this enables useful reports that let testing teams know how much of their code was executed during a test. This reporting may help identify which parts of their code need additional testing or more inspection, for example, with penetration testing. - Detecting memory corruption
Uncovering memory corruption issues is one of the strong suits of feedback-based fuzzing which is highly relevant for memory-unsafe languages such as C/C++. Nonetheless, fuzz testing is also very effective at securing memory-safe languages like Java and JavaScript. Check the list of bugs and vulnerabilities you can identify with fuzzing here. - Early bug detection – at unit, integration and system testing phases.
Feedback-based fuzzing tools can be integrated into the development process to test your code automatically as soon as you have an executable program. By leveraging the bug-finding capacities of fuzzing early, you can find bugs and vulnerabilities before they become a real problem.
Other Standards and Regulations that Recommend Fuzz Testing for Medical Devices
In Europe, similar initiatives, like the FDA, have been undertaken to address cybersecurity in medical devices. The European Commission, in collaboration with the Medical Device Coordination Group (MDCG), has issued guidance on cybersecurity for medical devices (MDCG 2019-16), emphasizing secure design, manufacturing, and testing methodologies, including fuzz testing.
 Chapter 3.7. Verification/Validation of MDCG 2019-16 – Guidance on Cybersecurity for Medical Devices.
Chapter 3.7. Verification/Validation of MDCG 2019-16 – Guidance on Cybersecurity for Medical Devices.
Fuzzing is also recommended in Medical Device and Health IT Joint Security Plan version 2 (JSP2) by the Healthcare and Public Health Sector Coordinating Council:
“Organizations should perform iterative testing of integrated components (third party or developed) to ensure that the components are tested at various integration stages. Integration testing involves building running versions of all components and their interfaces. Ideally, the build and test processes are automated into continuous integration pipelines, but less automated methods are also acceptable as long as the test system consists of the latest versions of developed components. Test plans can be consulted for specific tests that should be run iteratively throughout development and may include the following:
- Host vulnerability scanning, using tools like Nessus, to identify known vulnerabilities and insecure configurations;
- Dynamic Application Scanning Testing (DAST);
- Malformed Input Testing (e.g., Fuzz testing)".
In 2020, the International Medical Device Regulators Forum (IMDRF) published a technical document titled “Principles and Practices for Medical Device Cybersecurity” that included fuzz testing among the security testing methods.
Learn more about fuzz testing for medical devices here.
Explore code fuzz testing by Code Intelligence
Medical devices, machinery, automotive, and IoT manufacturers leverage Code Intelligence to test their products, effectively reducing the risk of delayed releases, costly fixes, malfunctions in critical systems, and cyber attacks. See fuzz testing in action by booking a free personalized demo with Code Intelligence experts.

.webp?width=408&height=327&name=White%20paper%20-%20Medical%20devices%20(mockup%20-%20high%20quality).webp)