Most modern vehicles are equipped with a variety of software systems and resemble sophisticated computers on wheels. The ISO/SAE 21434 standard is a framework that provides recommendations and requirements for secure software development in the automotive industry. But what is ISO 21434 exactly? And what can we expect from automotive software security in 2024? Read on and find out!
What is ISO/SAE 21434?
ISO/SAE 21434 has been developed by the International Standard of Organization (ISO) and the Society of Automotive Engineers (SAE) for the past couple of years. The ISO standard covers all software devices within the vehicle, as well as connectivity to external systems. Since existing norms and standards were developed in a time when vehicles did not yet heavily depend on software, they do not place too much value on its security.
ISO 21434 offers an approach that prioritizes security throughout the entire lifecycle of a vehicle. This means that both car manufacturers and original equipment manufacturers (OEMs) will need to display due diligence when it comes to the security of their software. ISO/SAE 21434 has rapidly created a standardized terminology for software security within the automotive landscape, defined minimal requirements for software security engineering, and requires dynamic software testing early in the product development lifecycle.
What has ISO/SAE 21434 brought us so far?
ISO/SAE 21434 was introduced in 2021. Judging its long-term effects is still a bit preliminary, but the framework has already brought us a couple of security improvements and benefits.
- The publication and (partial) implementation of the framework has incentivized many automotive organizations to implement more advanced security measures.
- An important achievement of ISO/SAE 21434 is that it has created a common language that allows companies to use standardized terminology. This allows manufacturers and suppliers to better align their cybersecurity activities.
- Because ISO/SAE 21434 is purposely abstract and leaves several parts of the actual cybersecurity design process in the hands of the user, it allows automotive companies to approach security from a variety of angles. This gives cybersecurity professionals the freedom to develop a cybersecurity system in line with their organization’s needs and resources.
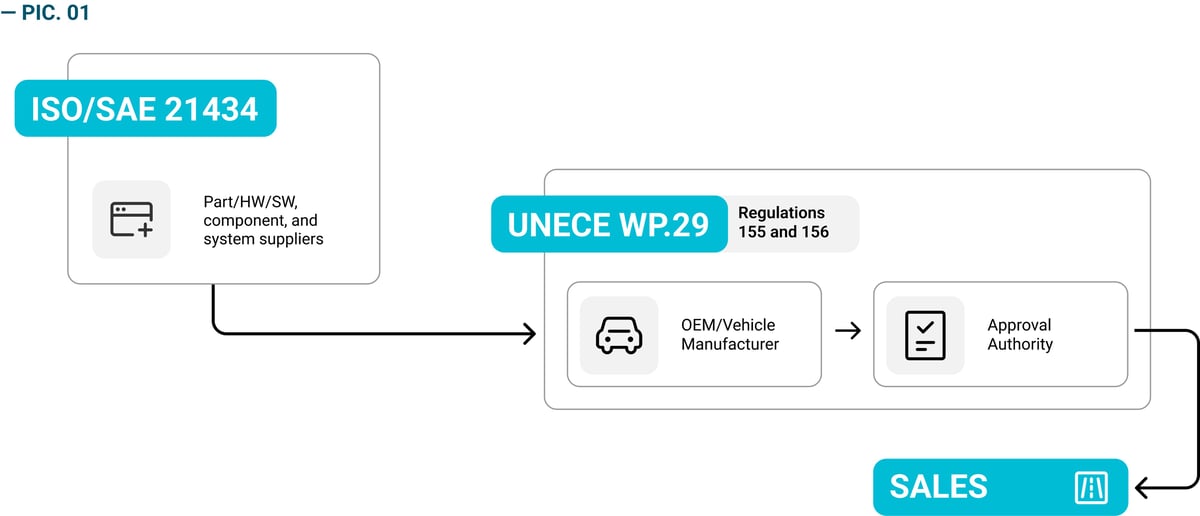
ISO/SAE 21434 and UN Regulation No. 155
Where the ISO/SAE 21434 is relevant for suppliers, the UN Regulation No. 155 (UN R155), which actually requires the setup and implementation of a management system that focuses on cybersecurity along vehicles, is important for OEMs. From July 2024, the UN R155 requirements for cybersecurity will apply to all vehicles in UNECE member states. UN R155 is also binding, whilst ISO/SAE 21434 consists of non-binding recommendations, although many automotive companies have contracts that require them to be ISO 21434 compliant. For example, one of ISO’s requirements explicitly recommends fuzz testing.
The mandates outlined in UNECE Regulations 155 and 156 (R155 and R156) are binding for vehicle manufacturers or Original Equipment Manufacturers (OEMs), who must comply to obtain type approval and, subsequently, access to markets. Failure to adhere to these regulations can result in sales bans. ISO/SAE 21434 serves as a guiding framework for companies supplying components to OEMs. If these suppliers adhere to the ISO/SAE 21434 standard, it helps the OEMs meet the criteria of R155 and R156, secure type approval, and gain subsequent market access.
The UN R155 states that:
- Automotive companies and OEMs have to develop a cybersecurity management system (CSMS) as part of the consideration of cybersecurity aspects in the type approval process.
- OEMs must demonstrate that the cybersecurity management system is used along the entire value chain. They are also accountable for applying the system in all of their daily operations.
- OEMs have to obtain a certificate of compliance for their CSMS every three years. An audit is part of the procedure.
Being and remaining compliant with ISO/SAE 21434
Being and remaining compliant with the ISO/SAE 21434 (and the UN R155) requires several actions from automotive companies and OEMs. First of all, it’s important to understand your current cybersecurity processes as comprehensively as possible. This allows you to define the right scope and develop effective action plans. Testing language subsets can be very useful in mitigating any activity that poses a security risk.
During the implementation phase, it is especially important to acquire and spread a general understanding of automotive cybersecurity within the whole of your organization. And last but not least: once processes have been implemented, keep monitoring them and make the right adjustments if the situation asks for it.
Which role does fuzzing play in ISO/SAE 21434 and UN R155 compliance?
There is little to no room for errors in modern automotive software. Source code fuzzing allows for accurate bug detection without the disadvantage of time-consuming false positives. It is a highly automated “shift-left” approach that paves the way for a decentralized testing culture. Fuzz testing is highly recommended for testing aimed at cybersecurity validation and verification. It minimizes unidentified weaknesses and vulnerabilities.
In ISO/SAE 21434, fuzz testing is specifically recommended for cybersecurity validation and verification during product development. One of the critical aspects of product development involves conducting code testing to minimize unidentified weaknesses and vulnerabilities in components. This is where fuzzing plays a crucial role. ISO/SAE 21434 suggests fuzz testing as a method for uncovering software weaknesses - as indicated in the requirement [RQ-10-12].
During the UNR155 type approval process manufacturers have to verify the sufficiency of cybersecurity measures by demonstrating their risk identification and testing practices. Here is where fuzzing comes in, since vehicle fuzzing can be viewed as an essential and comprehensive way to test if the system functions correctly, thereby verifying the sufficiency of security measures.
Due to its wide field of application, feedback-based fuzzing can be implemented at different steps of the software development lifecycle, making it the most attractive solution for vehicle manufacturers and OEMs and allowing them to take important steps towards ISO 21434 and UN R155 compliance.
.png?width=351&height=264&name=15%20(1).png) If you want to learn more about how fuzz testing contributes to ISO/SAE 21434 compliance, download the free white paper "How fuzz testing helps automotive companies comply with ISO/SAE 21434." Inside the white paper, you'll discover:
If you want to learn more about how fuzz testing contributes to ISO/SAE 21434 compliance, download the free white paper "How fuzz testing helps automotive companies comply with ISO/SAE 21434." Inside the white paper, you'll discover:
- The specifics of cybersecurity validation and verification requirements.
- How suppliers and OEMs comply with ISO.
- The benefits of source code fuzz testing, aka white-box fuzzing.

